Container Solutions is delighted to announce the open sourcing of a project we have been working on for some time.
Compliance Framework is an open source software suite designed to automate and manage your business's compliance tasks. You can think of it like Terraform and CI for software audit and compliance. It allows you to schedule, report, and define audit assessments, and gives you a framework to write your own compliance check 'providers' if they don't already exist.
In short, it allows you to achieve continuous compliance in your estate. Once your security policy is defined, you can track whether your applications are compliant, and not have to send assessors around with clipboards every six months to see if controls are still working as they were the last time you checked.
Why Build This?
Regular readers will know that we have written about the rise of compliance automation before. Automation is a core part of what unites and drives us at Container Solutions, and audit and compliance has historically been (relatively speaking) ignored by the open source world. While we typically 'automate all the things' to do with the software delivery lifecycle, we observed that there was a pattern of manual toil involved in Governance, Risk and Compliance (GRC) work associated with these projects that seemed resistant to automation.
The particular spark for us building this was an incident during one of our cloud transformation projects. A CISO of a major financial institution threw his hands up in a meeting and said 'there must be a better way to manage all this than manual checking of tables in confluence!' and a series of lightbulbs went off across the company.
We felt what was needed was an open source framework that allows business to manage their own compliance needs, which would deliver both cost savings for the GRC parts of their businesses, and improved visibility of the current state of compliance across the business (through real-time reporting).
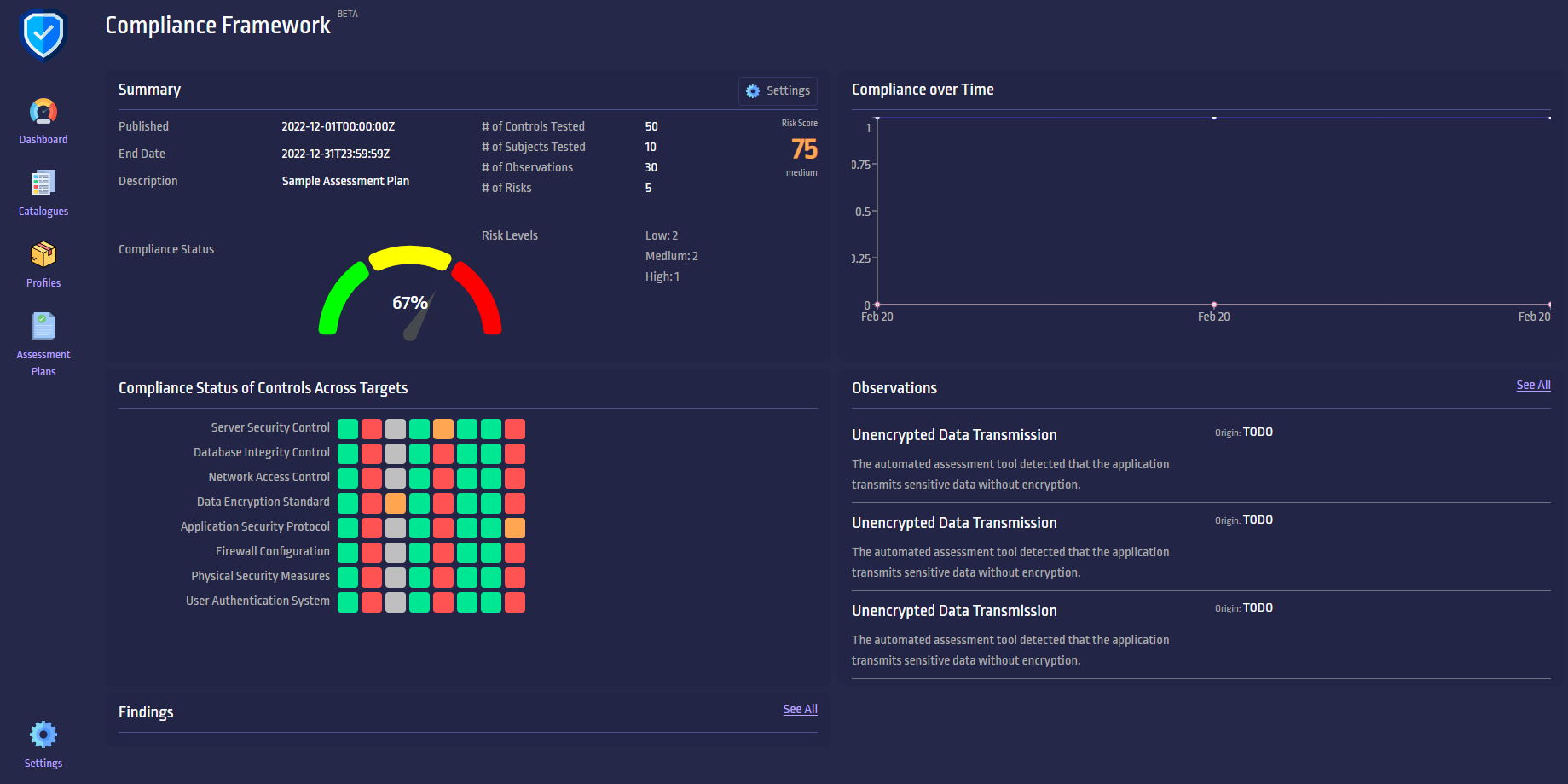
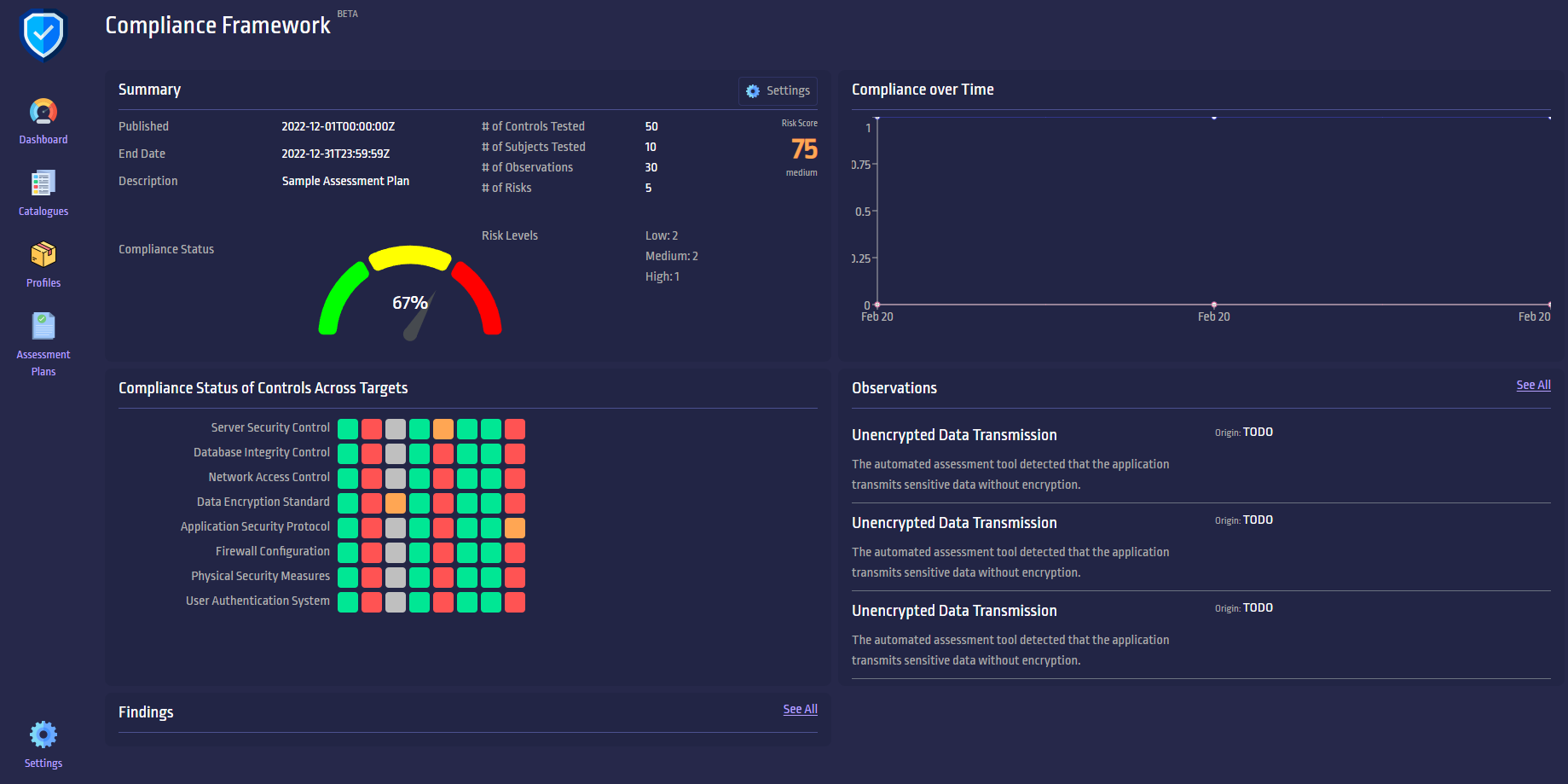
Some idea of this can be seen in this screenshot of a front end. We're not front-end engineers by trade, so help with this is definitely needed.
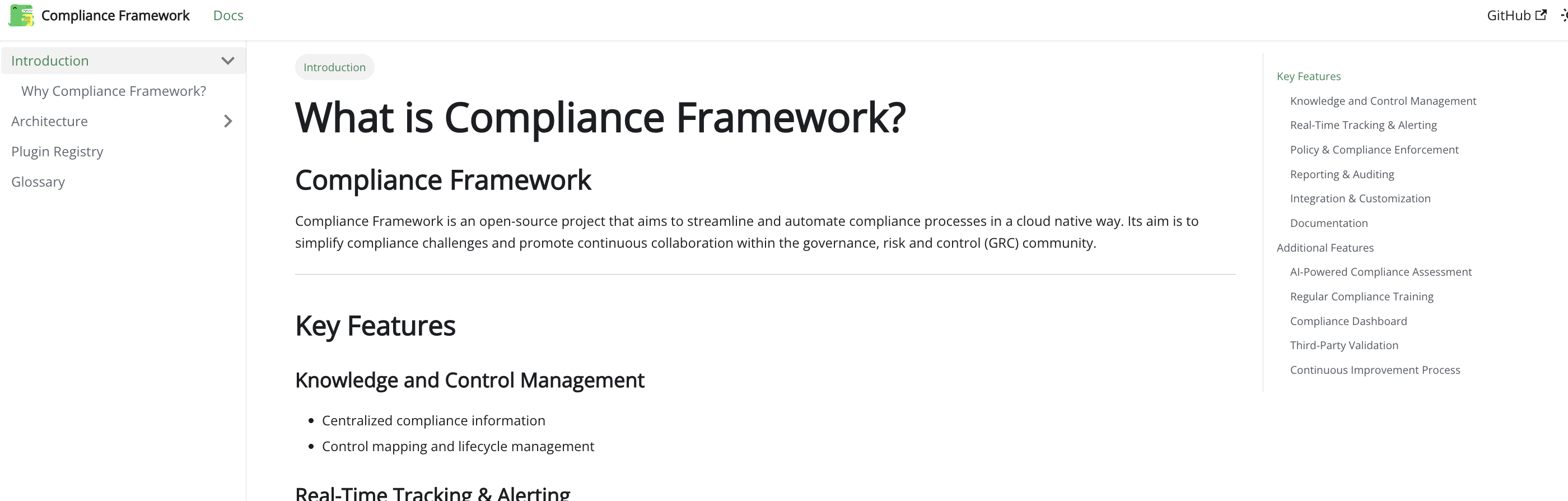
What Is It?
Compliance Framework consists of several discrete components which allow you to automate checks on whether controls are in place and working across your IT estate.
The architecture is documented here, but briefly there is a 'Core' and an 'Assessment Runtime'.
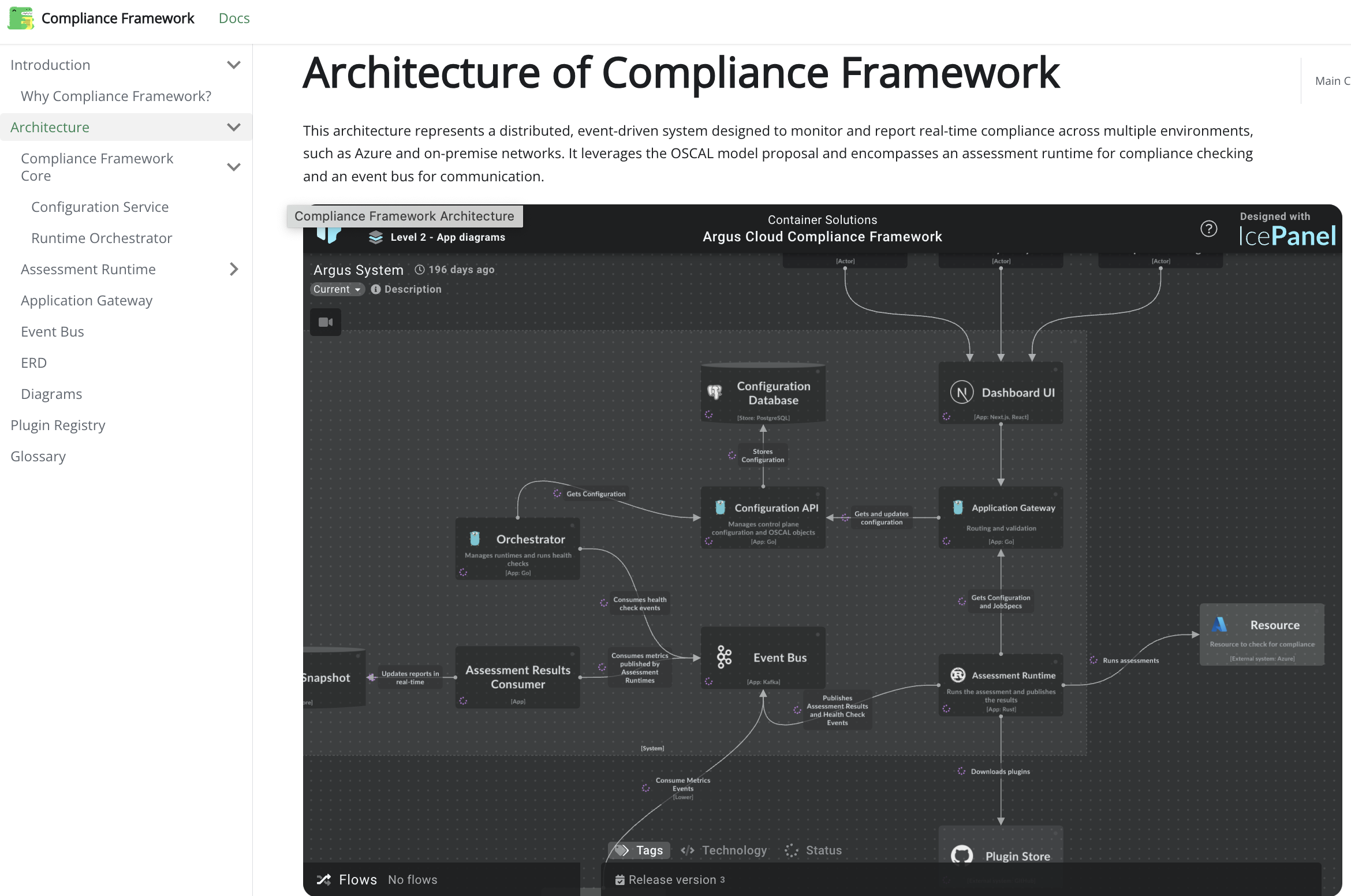
The Compliance Framework Core
In the core is a database that keeps track of 'Assessments', 'Controls', 'Components' and 'Attestations'. These are all OSCAL concepts, and the database is a JSON document-based one as that involves the least impedance mismatch with OSCAL standards.
The Configuration Service and the Runtime Orchestrator manage this database. The former provides an interface to keeping the database up to date, and the latter communicates via the Event Bus to the Assessment Runtime, ensuring the checks get carried out and results returned to the system.
The Assessment Runtime
This component runs the 'providers' or 'plugins' that are scheduled to run on the framework. For example, you might want to periodically check that all your disks are encrypted in AWS. In that case, you'd use the relevant provider, and the runtime would schedule and execute the run, sending the result back to the Core.
This separation is done in order to allow the runtime component to run on more constrained environments, where it can still perform checks with only needing one communication channel with the Core components (no need to open ssh from the constrained environment in order to perform VM checks).
Together, these components allow you run periodic checks against whatever you care about on your systems in a programmatic way. The results are then recorded and can be reported against retrospectively or in real time. These checks can be from generic standard 'providers', or you can build your own for your own niche use cases.
Key Features
Compliance Framework is built on a commitment to open standards. Container Solutions is a member of FINOS, the financial sector's open source foundation, and has been helping the development of common cloud controls, as well as contributing to discussions around the development of OSCAL (the 'Open Security Controls Assessment Language'), another emerging industry standard.
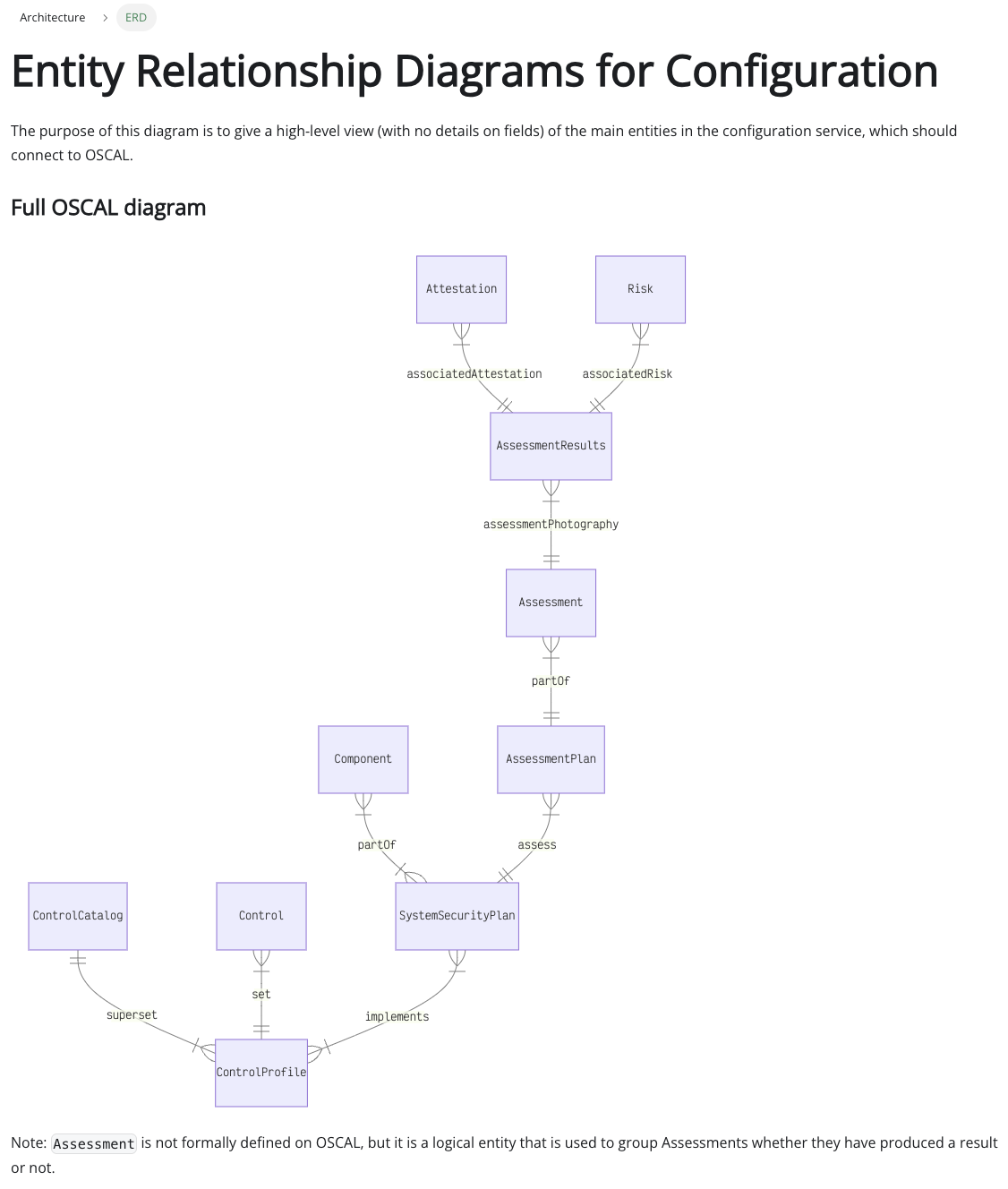
Compliance Framework has been built to support both of these initiatives. It helps turn those vital abstract standards into implemented realities that make managing compliance as efficient as other areas of Cloud Native software. bringing observability concepts (SLIs, SLOs, alerts) using the same Cloud Native standard as with any other Operational Activity. In addition, it is interoperable with other OSCAL-compatible tools in your compliance ecosystem.
Want to Know More?
If you'd like to know more, please get in touch, either through the socials or on this page, or the GItHub project directly:
https://github.com/compliance-framework/
Want to Get Involved?
Although many engineer-hours has been spent on this project already, we can definitely use help from others to get this project more traction. We are talking to various financial-sector companies about growing and implementing this the 'right way' and are keen to get more input on it.
While the back-end is functionality complete from an MVP point of view, we can of course always use help developing the APIs and improving the feature set. The area that could use the most help is the front end, which we are admittedly not the experts in, and could have a lot of impact on the project.

 Previous article
Previous article
